Understanding and Seeing your Infrastructure: Strategies for Effective Asset Mapping

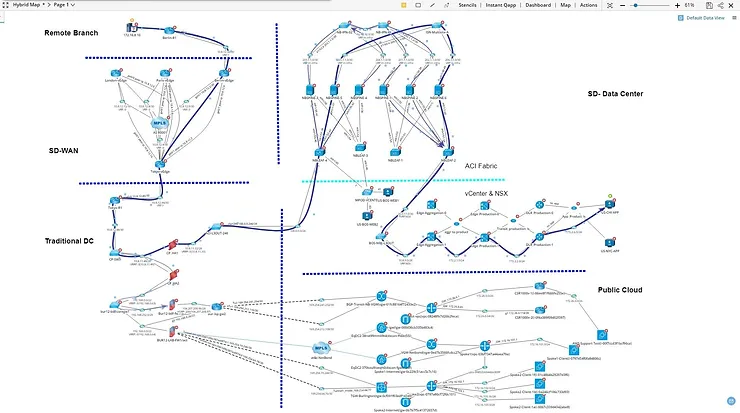
So, you have taken the first step of discovering your assets, what is the next layer of maturity? Well, it is time to map your assets. Asset mapping spans across the layers of a network, encompassing both Layer 2 (Data Link Layer) and Layer 3 (Network Layer) perspectives. This mapping allows you to have your first visualization of your Hybrid infrastructure.
We will delve into strategies for effective asset mapping, shedding light on the integrated approaches that bring together the best of both worlds, but also talk a little about how to approach mapping in a more methodical way.The Basics of Layer 2 and Layer 3 Mapping:
At the heart of IT asset mapping lies the ability to comprehend the physical and logical interconnections within a network. Layer 2 mapping involves understanding the Data Link Layer, focusing on MAC addresses, switch ports, and the physical connectivity of devices. On the other hand, Layer 3 mapping delves into the Network Layer, exploring IP addresses, routing tables, and logical connectivity.
Integrated Strategies:
- Network Mapping Tool (NMT):
- Implementing robust network mapping tool, bridges the gap between Layer 2 and Layer 3 mapping. These systems provide real-time visibility into device connectivity, network health, and traffic patterns. A holistic NMT can offer insights into the physical and logical aspects of your network, and help you visualize health, design and security gaps.
- Asset Management Systems:
- Integrating Asset Management Systems with mapping tools ensures a centralized repository of information. This combination allows for a seamless understanding of device configurations, physical locations, and network relationships. Asset Management Systems serve as the backbone for maintaining an up-to-date inventory of IT assets.
- Regular Audits and Documentation:
- Conducting regular audits and maintaining detailed documentation contribute to the accuracy of asset mapping. Networks evolve, and these integrated strategies provide a mechanism to validate and update information continually. Labeling physical devices and network ports enhances the overall clarity of the mapping.
The Value of Integration:
The true power of effective asset mapping emerges when all three of these strategies are integrated. The combination of people, process and technology integrated together ensures that as your organization changes and grows, you still have full visibility into your hybrid infrastructure. The immediate value of combining these approaches is that it enables organizations to:
-
Enhance Security:
-
Identify and monitor all devices connected to the network, facilitating swift detection of unauthorized or rogue devices. Security measures can be implemented more effectively when the entire network landscape is visible.
-
-
Optimize Troubleshooting:
-
Quickly pinpoint and isolate issues by understanding the physical and logical relationships between devices. This expedites the troubleshooting process, reducing downtime and reducing support costs by up to 50%.
-
-
Streamline Management:
-
A unified view of Layer 2 and Layer 3 mapping simplifies the management of IT assets. Centralized information promotes better decision-making, resource allocation, and strategic planning.
-
Now we know the strategies, but mapping an entire IT environment in one go can be overwhelming, especially in large and complex networks. Breaking down the mapping process into smaller, more manageable phases allows for a more systematic and controlled approach.
Recommended Approaches to Infrastructure Mapping:
1. Segmented Mapping:
-
Divide the network into logical segments or VLANs. Start by mapping one segment at a time. This approach is particularly useful for large organizations with diverse network architectures.
2. Critical Infrastructure First:
-
Prioritize mapping critical infrastructure, such as servers, routers, and switches. Understanding the core components of the network provides a foundational understanding before moving on to less critical or peripheral devices.
3. Location-Based Mapping:
-
Begin mapping assets based on physical locations. This approach is suitable for organizations with multiple offices or branches. Mapping assets within a specific location helps in understanding the local network structure.
4. Priority-Based Mapping:
-
Prioritize mapping assets based on their importance to business operations or security. Begin with mission-critical systems and gradually move towards less critical assets. This approach aligns with risk management principles.
5. Project-Based Mapping:
-
Associate mapping efforts with specific projects or initiatives. For example, when implementing a new application or service, focus on mapping the relevant components associated with that project.
6. Problem-Solving Mapping:
-
When troubleshooting or addressing specific issues, focus on mapping the relevant network segments associated with the problem. This targeted approach helps in quickly identifying and resolving issues.
These are just a few mapping approaches, that organizations can use to avoid the challenges associated with attempting to map the entire environment in one go. This phased strategy allows for better control, more accurate results, and a systematic understanding of the network landscape over time.
Look, navigating the complex web of your hybrid IT environment requires a comprehensive understanding of both Layer 2 and Layer 3 perspectives. Discovering your assets and mapping them provide the foundational data to improving IT support, security, operations, but more importantly the bottom line.